Разделы презентаций
- Разное
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Геометрия
- Детские презентации
- Информатика
- История
- Литература
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
Defense in Depth: Windows 8.1 Security
Содержание
- 1. Defense in Depth: Windows 8.1 Security
- 2. Jump Start AgendaModule 1: Today’s
- 3. Module InsightsWe will talk about the rapidly
- 4. Erdal Ozkaya@Erdal_OzkayaKEMP TechnologiesCharles Sturt UniversityMicrosoft MVPCertified Ethical Hacker
- 5. Слайд 5
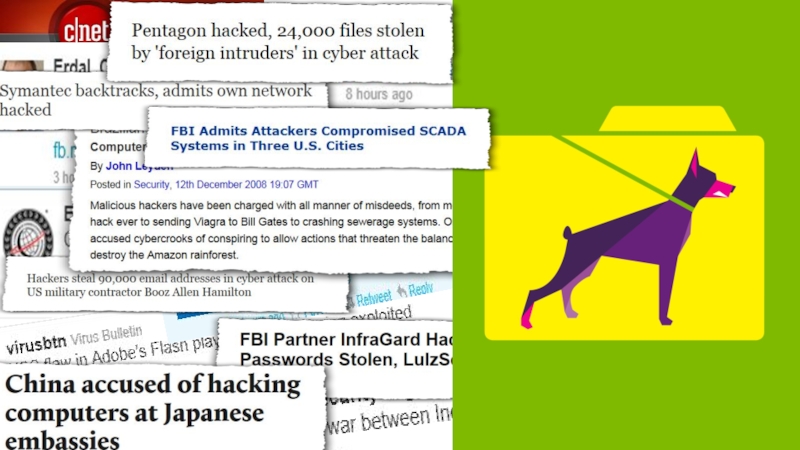
- 6. How do you get hacked?
- 7. Warning! This Presentation Contains many information which
- 8. Target AudienceThis course is helpful for anyone
- 9. The threat landscape is changing rapidly.
- 10. Mobility represents the end perimeter based security.Your perimeter is fading, maybe it’s already gone.
- 11. BYOD is a top priority and one
- 12. The improvements that we’ve made in the Windows platforms have driven our adversaries to new tactics.
- 13. Attackers have set their sights on identity theft and they’re breaking into systems as you!
- 14. BankingSmall Online BusinessSmall Online
- 15. Need to knows on complex passwords…
- 16. There is a prolific and easily accessible
- 17. Слайд 17
- 18. And so we have a perfect storm.
- 19. Слайд 19
- 20. Key Takeaways
- 21. @ErdalOzkaya@MiladPFEConnect with the speakers!http://erdalozkaya.com/https://www.facebook.com/milad.aslaner
- 22. Deep technical content and free product evaluationsHands-on
- 23. Слайд 23
- 24. Скачать презентанцию
Слайды и текст этой презентации
Слайд 1Erdal Ozkaya | Most Valuable Professional, KEMP Technologies
Milad Aslaner |
Premier Field Engineer, Microsoft
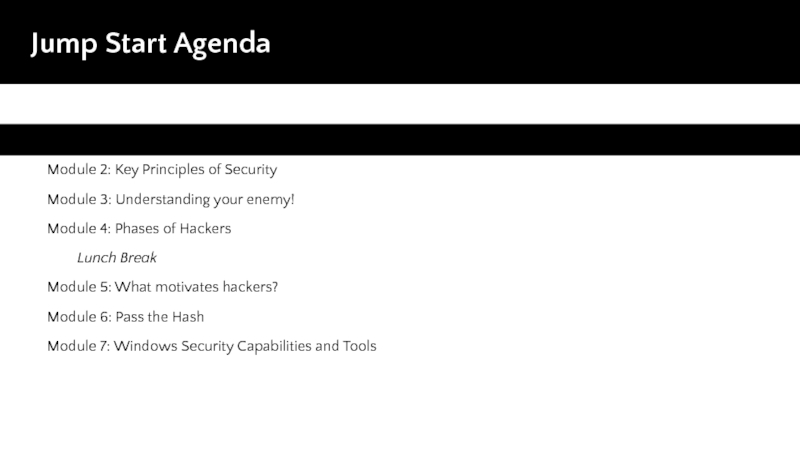
Слайд 2 Jump Start Agenda
Module 1: Today’s Threat Landscape
Module 2:
Key Principles of Security
Module 3: Understanding your enemy!
Module 4: Phases
of HackersLunch Break
Module 5: What motivates hackers?
Module 6: Pass the Hash
Module 7: Windows Security Capabilities and Tools
Слайд 3Module Insights
We will talk about the rapidly changing threat landscape
and the importance of strong mitigation capabilities.
Слайд 4Erdal Ozkaya
@Erdal_Ozkaya
KEMP Technologies
Charles Sturt University
Microsoft MVP
Certified Ethical Hacker
Слайд 7Warning! This Presentation Contains many information which you should not use
in live targets or networks without permissions.
Слайд 8Target Audience
This course is helpful for anyone interested in security,
particularly IT Pros and Security Architects at mid-sized and enterprise
organizations.Слайд 9The threat landscape is changing rapidly. But this time it’s
not just the attackers driving change, it’s your users.
Слайд 10Mobility represents the end perimeter based security.
Your perimeter is fading,
maybe it’s already gone.
Слайд 11BYOD is a top priority and one of the biggest
challenges
But it’s not the only one when it comes to
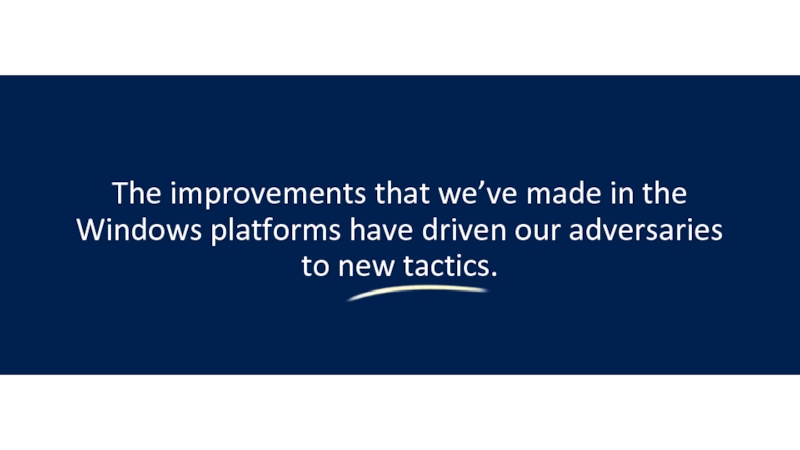
security.Слайд 12The improvements that we’ve made in the Windows platforms have
driven our adversaries to new tactics.
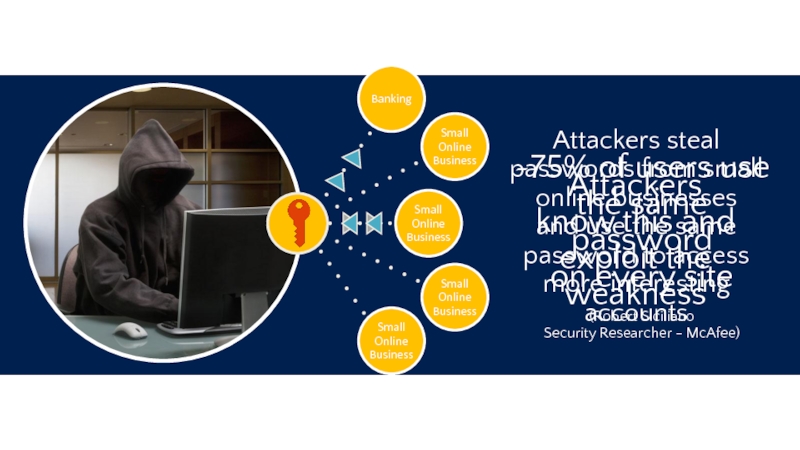
Слайд 14Banking
Small
Online
Business
Small
Online
Business
Small
Online
Business
Small
Online
Business
~75% of
users use the same password
on every site
(Robert Siciliano
Security Researcher - McAfee)
Attackers know this and exploit the weakness
Attackers steal passwords from small online businesses
and use the same password to access more interesting accounts
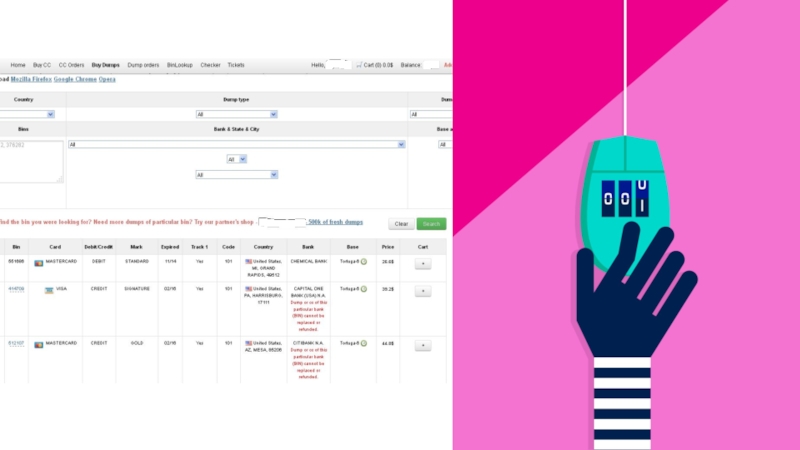
Слайд 16There is a prolific and easily accessible black market that
facilitates the buying and selling of identities, credit cards, etc.
Personal information about you can almost certainly be found there!
Слайд 21@ErdalOzkaya
@MiladPFE
Connect with the speakers!
http://erdalozkaya.com/
https://www.facebook.com/milad.aslaner
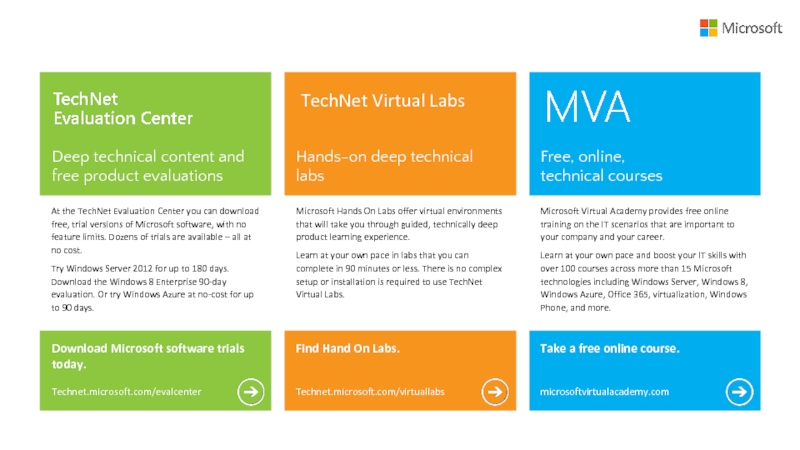
Слайд 22Deep technical content and free product evaluations
Hands-on deep technical labs
Free,
online,
technical courses
Download Microsoft software trials today.
Find Hand On Labs.
Take
a free online course.Technet.microsoft.com/evalcenter
Technet.microsoft.com/virtuallabs
microsoftvirtualacademy.com
At the TechNet Evaluation Center you can download free, trial versions of Microsoft software, with no feature limits. Dozens of trials are available – all at no cost.
Try Windows Server 2012 for up to 180 days. Download the Windows 8 Enterprise 90-day evaluation. Or try Windows Azure at no-cost for up to 90 days.
Microsoft Hands On Labs offer virtual environments that will take you through guided, technically deep product learning experience.
Learn at your own pace in labs that you can complete in 90 minutes or less. There is no complex setup or installation is required to use TechNet Virtual Labs.
Microsoft Virtual Academy provides free online training on the IT scenarios that are important to your company and your career.
Learn at your own pace and boost your IT skills with over 100 courses across more than 15 Microsoft technologies including Windows Server, Windows 8, Windows Azure, Office 365, virtualization, Windows Phone, and more.
TechNet Virtual Labs