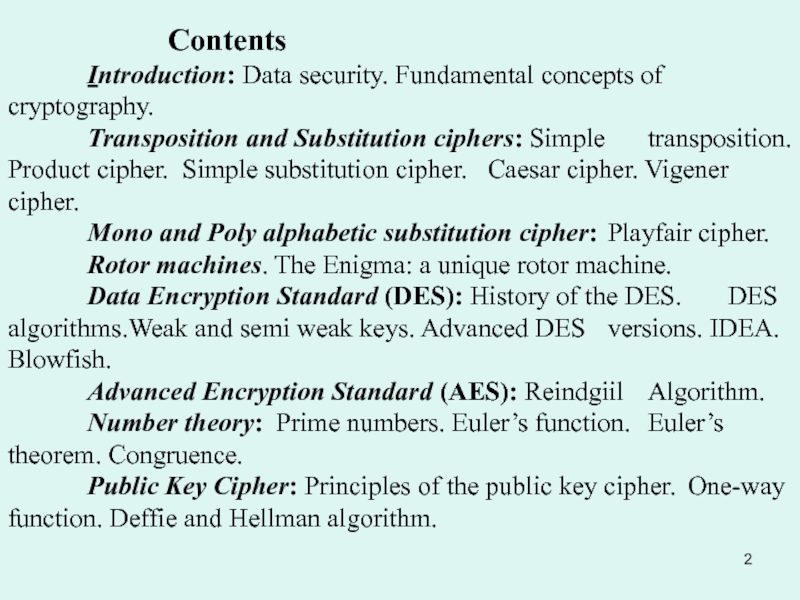
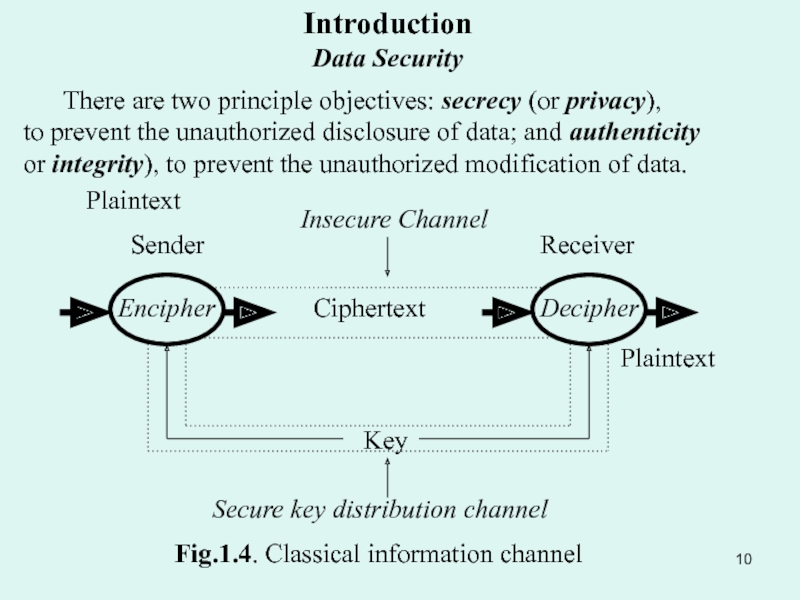
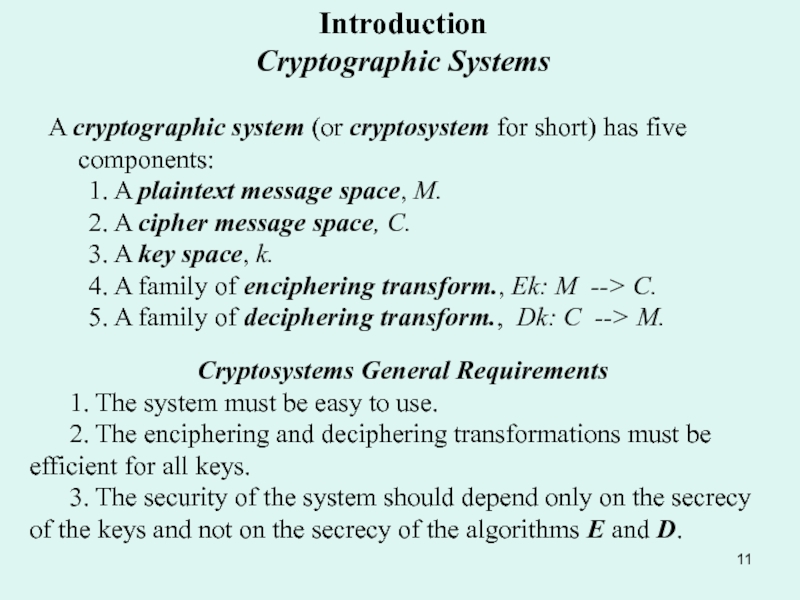
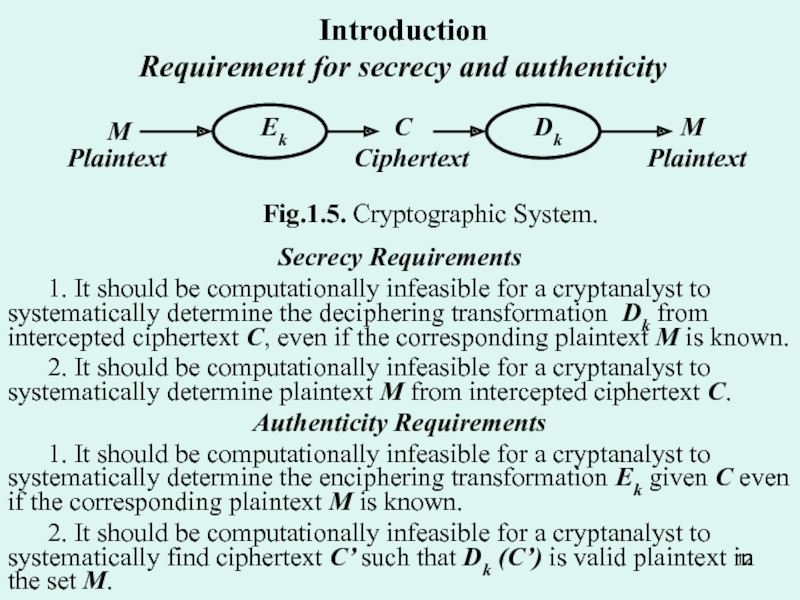
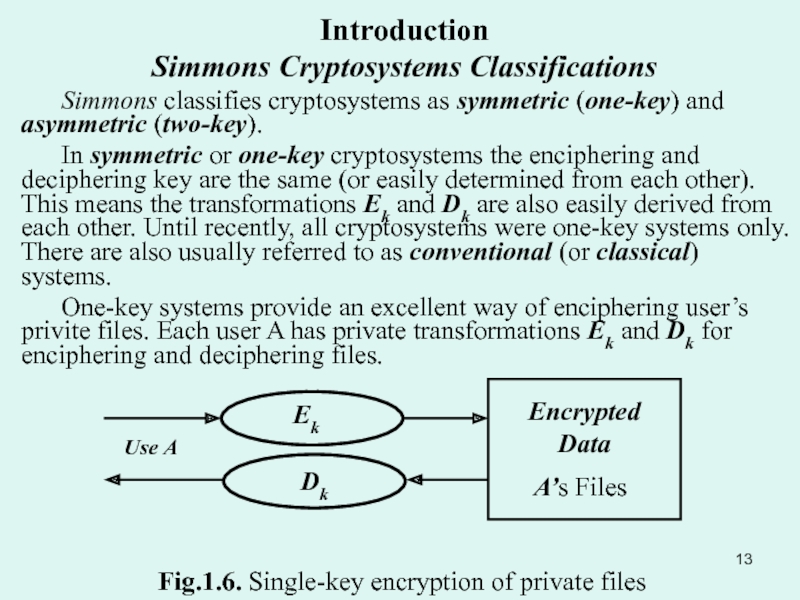
Substitution ciphers: Simple transposition. Product cipher. Simple substitution
cipher. Caesar cipher. Vigener cipher.Mono and Poly alphabetic substitution cipher: Playfair cipher.
Rotor machines. The Enigma: a unique rotor machine.
Data Encryption Standard (DES): History of the DES. DES algorithms.Weak and semi weak keys. Advanced DES versions. IDEA. Blowfish.
Advanced Encryption Standard (AES): Reindgiil Algorithm.
Number theory: Prime numbers. Euler’s function. Euler’s theorem. Congruence.
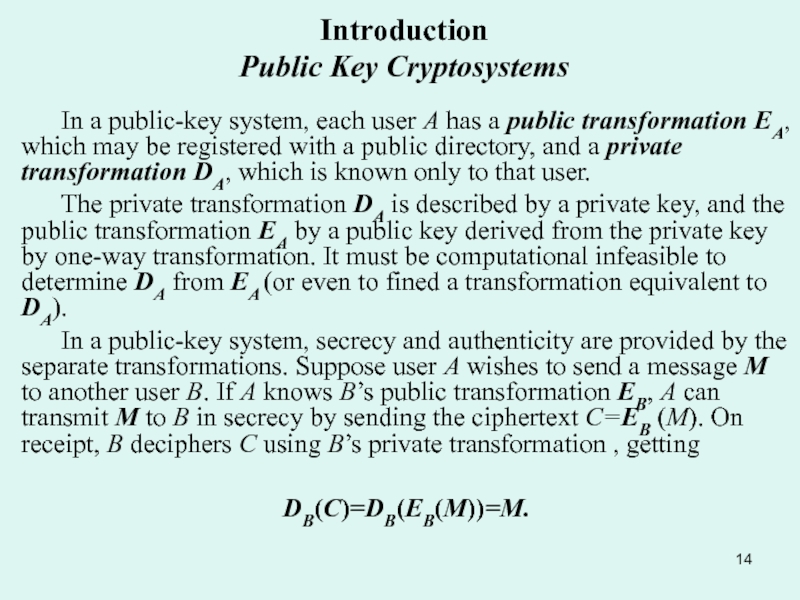
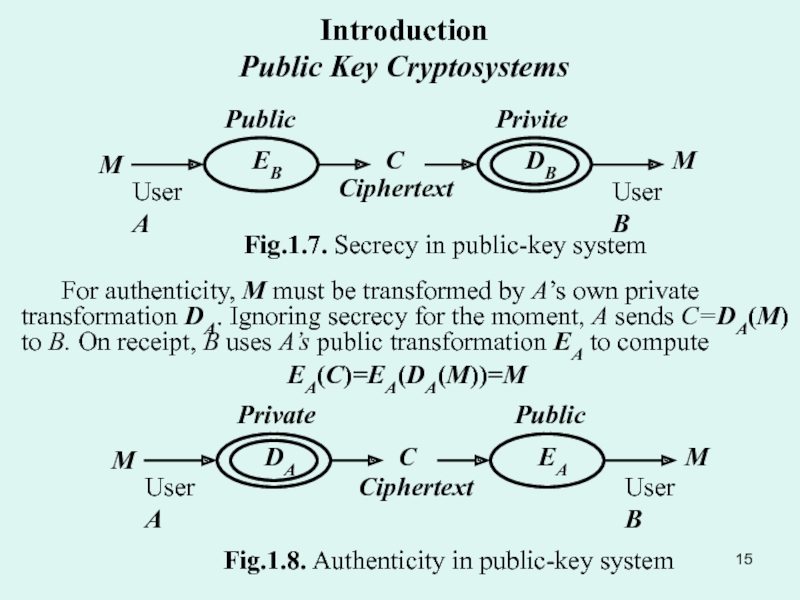
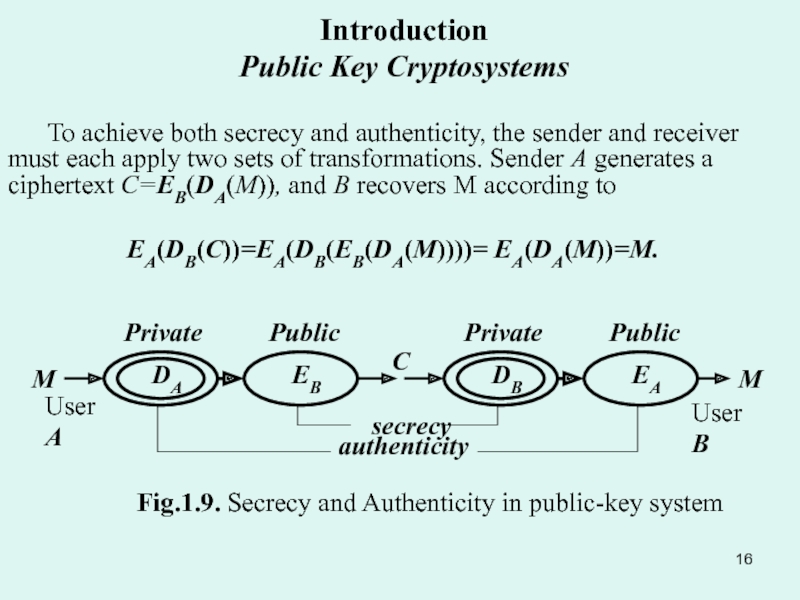
Public Key Cipher: Principles of the public key cipher. One-way function. Deffie and Hellman algorithm.