online,
technical courses
Download Microsoft software trials today.
Find Hand On Labs.
Take
a free online course.
Technet.microsoft.com/evalcenter
Technet.microsoft.com/virtuallabs
microsoftvirtualacademy.com
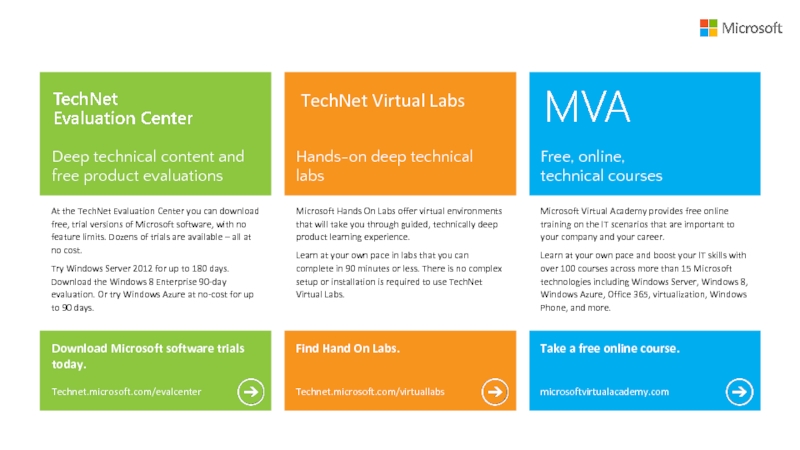
At the TechNet Evaluation Center you can download free, trial versions of Microsoft software, with no feature limits. Dozens of trials are available – all at no cost.
Try Windows Server 2012 for up to 180 days. Download the Windows 8 Enterprise 90-day evaluation. Or try Windows Azure at no-cost for up to 90 days.
Microsoft Hands On Labs offer virtual environments that will take you through guided, technically deep product learning experience.
Learn at your own pace in labs that you can complete in 90 minutes or less. There is no complex setup or installation is required to use TechNet Virtual Labs.
Microsoft Virtual Academy provides free online training on the IT scenarios that are important to your company and your career.
Learn at your own pace and boost your IT skills with over 100 courses across more than 15 Microsoft technologies including Windows Server, Windows 8, Windows Azure, Office 365, virtualization, Windows Phone, and more.
TechNet Virtual Labs



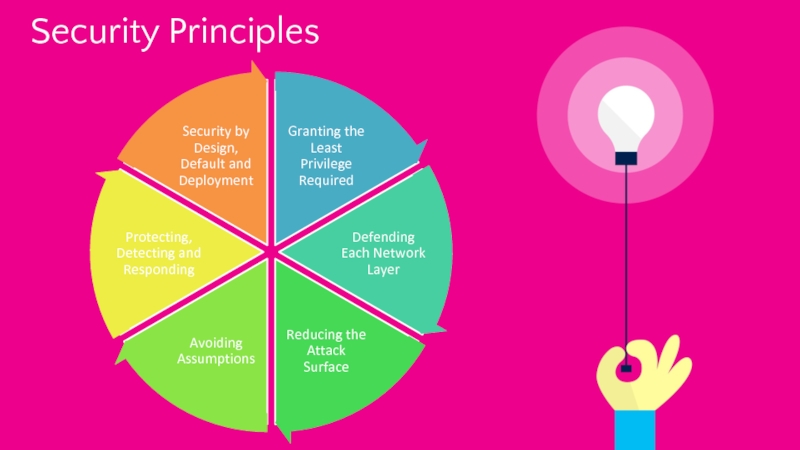
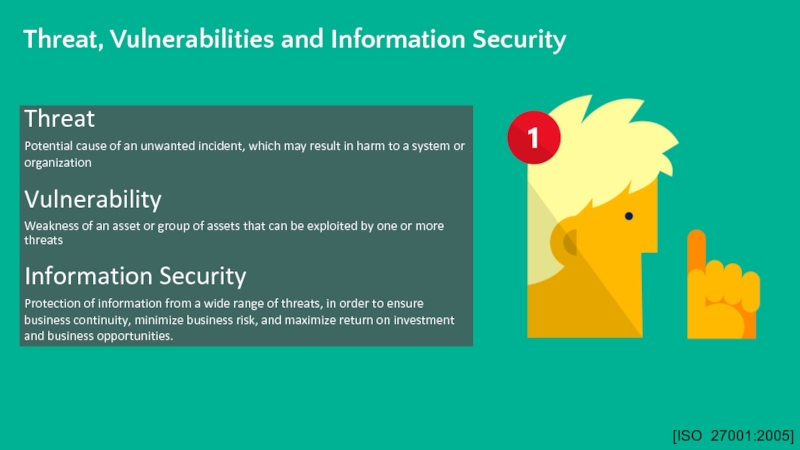
![Key Principles of Security [ISO 27001:2005, Clause 3.1]Define elements of valueAsset [ISO 27001:2005, Clause 3.1]Define elements of valueAsset](/img/thumbs/7b85f02a7b3ff17bffca72f63d779e97-800x.jpg)
![Key Principles of Security [ISO 27001:2005, Clause 3.1]Identification of AssetsA possible classification [ISO 27001:2005, Clause 3.1]Identification of AssetsA possible classification](/img/thumbs/ea2f4bfa6eff0dc4ca0ff210053039c0-800x.jpg)

![Key Principles of Security [ISO 27005– 8.2.1] [ISO 27005– 8.2.1]](/img/tmb/4/359592/c2edda7e2883e91894f8576681222fff-800x.jpg)