Разделы презентаций
- Разное
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Геометрия
- Детские презентации
- Информатика
- История
- Литература
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
Cyber Spying in world today
Содержание
- 1. Cyber Spying in world today
- 2. ContentCyber spyingSpywareFeatures of functioningHistory and developmentScope of UseMethods of treatment and preventionReference
- 3. Cyber spyingCyberespionage or computer spying (also used
- 4. SpywareSpyware (spyware software) - a program that
- 5. Features of functioningSpyware can carry out a
- 6. HISTORY AND DEVELOPMENT
- 7. History and developmentAccording to AOL and National
- 8. History and developmentBy 2006, spyware have become
- 9. SCOPE OF USEAmong the possible applications of "potentially unwanted technologies" is both legitimate and fraudulent.
- 10. LEGITIMATE APPLICATIONSTracking Software (tracking software) is widely
- 11. DIGITAL COPYRIGHT PROTECTION
- 12. METHODS OF TREATMENT AND PREVENTION
- 13. MEASURES TO PREVENT INFECTION
- 14. ReferenceCyber Spying. Copyright © Wikipedia 2001-2015. Retrieved
- 15. THANK YOU FOR YOUR ATTENTION
- 16. Скачать презентанцию
Слайды и текст этой презентации
Слайд 2Content
Cyber spying
Spyware
Features of functioning
History and development
Scope of Use
Methods of treatment
and prevention
Слайд 3Cyber spying
Cyberespionage or computer spying (also used the term "cyber
reconnaissance") - a term denoting tend to steal information in
order to obtain personal, economic, political or military superiority, carried out with the use of bypass (hacking) computer security systems, with the use of malware software, including "Trojan horses" and spyware. Typically, cyber-espionage operations are illegal in the country of victim, while in the aggressor country they are support at the highest levels.Слайд 4Spyware
Spyware (spyware software) - a program that surreptitiously installed on
your computer to collect information about your computer configuration, user,
user activity without consent. Can also perform other actions: changing the settings, software installation without the user's knowledge, redirecting user actions. Now, there are many definitions and interpretations of the term spyware.Слайд 5Features of functioning
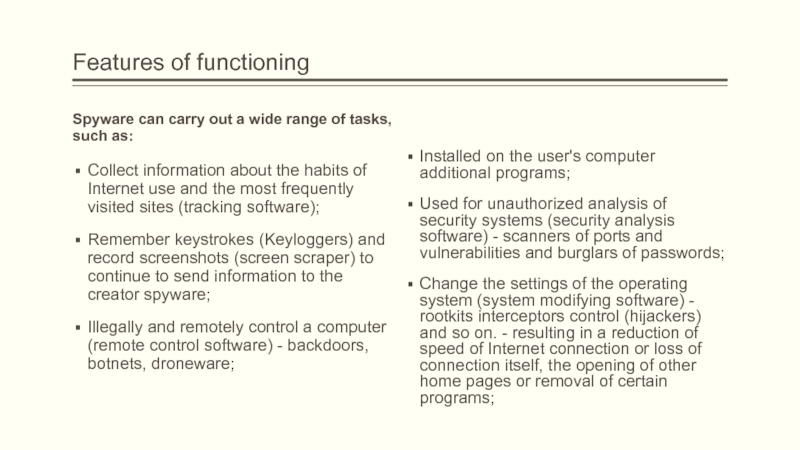
Spyware can carry out a wide range of
tasks, such as:
Collect information about the habits of Internet use
and the most frequently visited sites (tracking software);Remember keystrokes (Keyloggers) and record screenshots (screen scraper) to continue to send information to the creator spyware;
Illegally and remotely control a computer (remote control software) - backdoors, botnets, droneware;
Installed on the user's computer additional programs;
Used for unauthorized analysis of security systems (security analysis software) - scanners of ports and vulnerabilities and burglars of passwords;
Change the settings of the operating system (system modifying software) - rootkits interceptors control (hijackers) and so on. - resulting in a reduction of speed of Internet connection or loss of connection itself, the opening of other home pages or removal of certain programs;
Слайд 7History and development
According to AOL and National Cyber-Security Alliance of
2005, 61% of respondents of computers contain some form of
spyware, of which 92% of users were not aware of presence spyware on their machines, and 91% reported that they did not give permission for the installation of spyware.Слайд 8History and development
By 2006, spyware have become one of the
prevailing threats to the security of computer systems using Windows.
Computers in which Internet Explorer serves as the main browser are partially vulnerable not because Internet Explorer is most widely used, but due to the fact that its tight integration with Windows allows spyware access to key nodes OS.Слайд 9SCOPE OF USE
Among the possible applications of "potentially unwanted technologies"
is both legitimate and fraudulent.
Слайд 10LEGITIMATE APPLICATIONS
Tracking Software (tracking software) is widely used and legal
for monitoring PCs.
Adware can openly be included in composition of
free and shareware software. The user agrees to view advertising to have any further opportunity (for example - to use this program free of charge). In this case, the presence of adware should clearly prescribed in the end-user agreement (EULA).Software modifications to the system can used for personalization of the desired user.
Program the remote control and monitoring can used for remote technical support or access to their own resources, which are located on the remote computer.
Program for automatic download can used to automatically updates, applications and OS updates.
Program for the analysis of security systems used to study the vulnerability of computer systems and other perfectly legitimate purposes.
Passive tracking technologies may be useful to personalize web pages visited by user.