Разделы презентаций
- Разное
- Английский язык
- Астрономия
- Алгебра
- Биология
- География
- Геометрия
- Детские презентации
- Информатика
- История
- Литература
- Математика
- Медицина
- Менеджмент
- Музыка
- МХК
- Немецкий язык
- ОБЖ
- Обществознание
- Окружающий мир
- Педагогика
- Русский язык
- Технология
- Физика
- Философия
- Химия
- Шаблоны, картинки для презентаций
- Экология
- Экономика
- Юриспруденция
Information security
Содержание
- 1. Information security
- 2. Plan1. Information security2. The Information Security Concept of Kazakhstan3. Сlassification of threats and attacks
- 3. Information Security — state preservation of state
- 4. Information security, sometimes shortened to InfoSec, is
- 5. Слайд 5
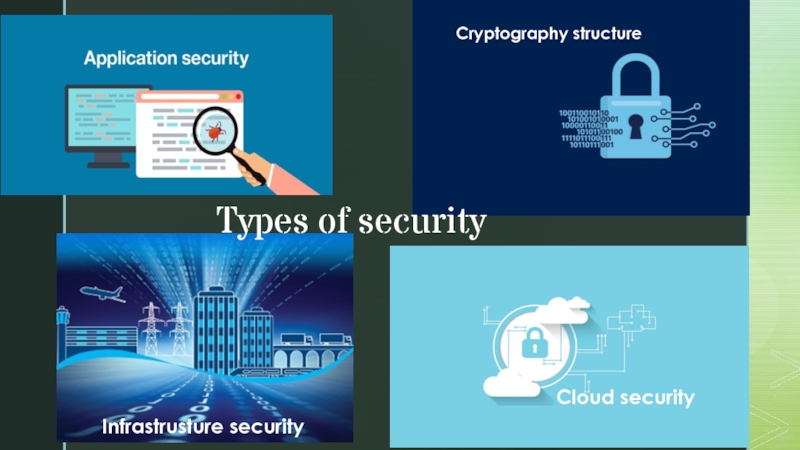
- 6. Types of securityCryptography structureInfrastrusture securityCloud security
- 7. The list of main goals and tasks,
- 8. By the Decree of the President of
- 9. Since Kazakhstan gained independence, the protection of
- 10. The main acts of the Republic of
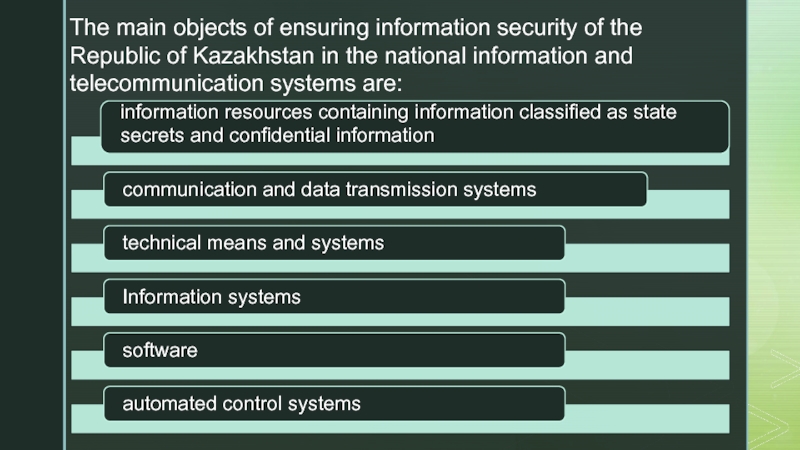
- 11. The main objects of ensuring information security
- 12. Risk: A possibility that a threat exploits
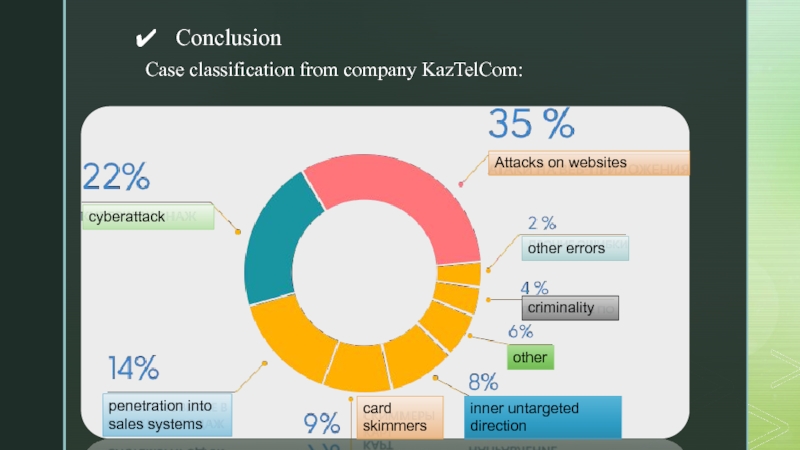
- 13. cyberattackAttacks on websitesother errorspenetration into sales systemscard skimmersinner untargeted directionothercriminalityCase classification from company KazTelCom:Conclusion
- 14. Thanks for
- 15. Скачать презентанцию
Слайды и текст этой презентации
Слайд 1Information security
Kenzhebaeva Moldir
Kystaubaeva Makpal
Ruzahunova Sabina
Kudaikulova Saltanat
Слайд 2Plan
1. Information security
2. The Information Security Concept of Kazakhstan
3. Сlassification
of threats and attacks
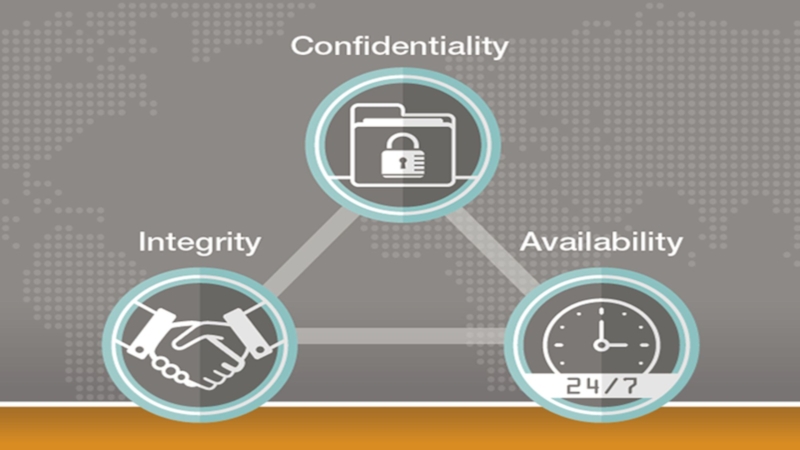
Слайд 3Information Security — state preservation of state information resources and
security
legal rights of the individual and society in the information
sphere.Слайд 4Information security, sometimes shortened to InfoSec, is the practice of
preventing unauthorized access, use, disclosure, disruption, modification, inspection, recording or
destruction of information.The information or data may take any form, e.g. electronic or physical.
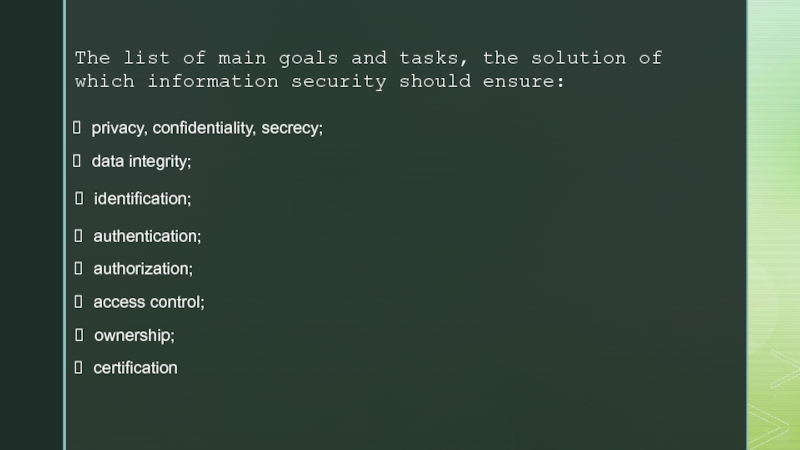
Слайд 7The list of main goals and tasks, the solution of
which information security should ensure:
privacy, confidentiality, secrecy;
data integrity;
identification;
authentication;
authorization;
access control;
ownership;
certification
Слайд 8By the Decree of the President of the Republic of
Kazakhstan of October
10, 2006 No. 1999 , the Information
Security Concept of the Republic of Kazakhstan was approved. The concept serves as the basis for the formation and implementation of a unified state policy of the Republic of Kazakhstan in the field of information security, its provisions should be considered when creating and developing a unified information space of Kazakhstan and further improving the state of information policy.Слайд 9Since Kazakhstan gained independence, the protection of state secrets has
been one of the main tasks of the National Security
Committee. Thus, at the initiative of the National Security Committee, in 1992 the State Technical Commission for Information Protection under the Cabinet of Ministers of the Republic of Kazakhstan was established with broad powers to coordinate work in the field of state secret protection.Слайд 10The main acts of the Republic of Kazakhstan that governs
legal relations in the field of information security are:
1) the
laws of the Republic of Kazakhstan “On State Secrets”, “On Electronicdocument and electronic digital signature”,“On informatization”,“On technical
regulation","On licensing","On the media ","On communication"
2) sectoral program in the field of protection of state secrets;
3) sectoral program to ensure the information security;
4) Program for the development of information and communication technologies in
Republic of Kazakhstan for 2010 - 2016, approved by the Government;
5) strategic plans of state bodies.